As the entire world anxiously monitors and battles the spread of the Coronavirus (COVID-19) with all its resources, it seems that the novel virus continues to bring growing concerns to every home and industry alike.
Today in the Tech world, cybercriminals are preying on the increasing global fears and misconceptions surrounding the virus. Using sophisticated Coronavirus-themed phishing emails, they’re launching some of the most successful phishing campaigns ever witnessed.
According to Check Point researchers, “Since January 2020, there have been over 4,000 coronavirus-related domains registered globally’’ Meanwhile, these domains are 50% more likely to be malicious than other domains, researchers added.
The European Central Bank also issued a letter warning financial institutions about increases in Coronavirus-themed phishing and other related cybercrimes.
And Just like the Coronavirus, these phishing emails are spreading out to many of our inboxes at a remarkable rate. Meanwhile, the current ‘Coronamania’ is only fuelling their success and prompting more and more people to fall for them.

To protect yourself and your staff from these phishing scams, we advise you to share this piece with your colleagues and everyone at your organisation.
‘Stay alert and help others take the same necessary cybersecurity precautions.’
Unfortunately, hackers and threats actors are continuously updating and adjusting their sly messaging in line with global response and recent Coronavirus developments. That’s why you not only need to be aware of the following phishing scams, but also consider them a guiding reference to what you should be looking out for at the moment.


These emails typically contain a malicious attachment or link labeled things like ‘Coronavirus Precautions’ or ‘Donate to Coronavirus Response Plan’. They then infect your system with a Malware.
WHO has stated that it will NEVER ask for direct donations to emergency response plans via email, separate websites, calls or texts. WHO instead advises you to:
A. Verify the sender by checking their email address
B. Checking any links before clicking
C. Don’t provide any personal information
D. Report any scams you see to their attorney general office
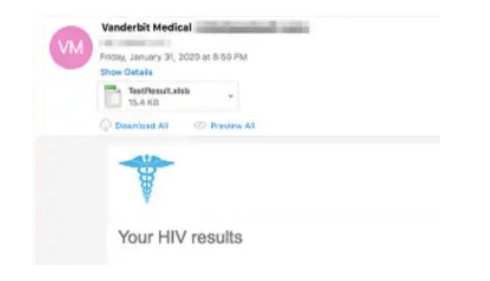
These emails are targeting various companies in the healthcare, pharmaceutical and insurance industries. They carry a malicious attachment labelled ‘test results’ which infects your system with a Koadic RAT.
Attackers are then able to run programs and access your data, including sensitive personal and financial information.
As threat actors keep changing things, you’d want to stay alert to similar emails that might arouse suspicion. Remember, ALWAYS double-check the sender.

If a COVID-19 cure or vaccine is found, trust me, you’re going to hear about it from a legitimate news source first. Anything other than that is simply bogus.
Remember, with great panic comes great conspiracy theories. However, when a conspiracy theory is delivered straight to your email inbox, it’s rather a conspiracy scam out to get YOU.

In line with the growing need for employees to work from home, employees are receiving phishing emails impersonating their HR departments or executives.
Such emails typically ask you to sign into DocuSign or Microsoft Word, which then steals your credentials, according to Buzzfeed News.
Before opening any suspicious or unrequested email from your HR department, double-check the sender. You may need to directly contact your HR department via a trusted email you’ve been using (or via telephone, if possible) to confirm the legitimacy of the email you received.
MalwareHunterTeam discovered another campaign of Coronavirus-themed emails impersonating the Center for Public Health of the Ministry of Health of Ukraine.
These emails embed a three-page Coronavirus-themed Microsoft Office document about the Coronavirus.
According to MalwareHunterTeam, the document contains malicious macros that can drop a backdoor with capabilities such as clipboard stealing, keylogging, and the ability to take screenshots from a victim’s computer.

1. Awareness is the best weapon to protect yourself and your company from the danger of phishing emails. Make sure you’re aware of the current phishing trends and raise your employees’ awareness about how to best deal with them.
2. Security Tools like GAT can help save your domain if any users ever fall for these emails. While GAT+ won’t stop spam or phishing emails, if one gets in, it enables Admins to instantly remove it from every account on your G Suite domain, preventing further damage.
Learn more about how GAT can help your G Suite Users work better and safer remotely here.



